New version of mobile malware Catelites possibly linked to Cron cyber gang
20 DEC 2017
New malware targets accounts at over 2,200 financial institutions
Co-authored with Nikolaos Chrysaidos, Head of Mobile Threats & Security, Avast
In May 2017, Russian authorities arrested twenty members of a cybercriminal gang who had been using a banking Trojan called “CronBot” to steal over $900,000. The gang hid the Trojan within a host of phony apps, some designed to look like authentic online banking apps, some designed to look like pornography apps. These thieves knew their target demographic: over one million unsuspecting users installed the malware onto their Android mobile devices. The good news is that the villainous gang has been apprehended. The bad news is that the villainous malware is still at large.
Now, we have uncovered and analyzed a new version of the malware, dubbed Catelites Bot, which shares similarities with the malware used for CronBot. While we have no hard evidence that the Catelites actor is linked to Cron, it is likely that Cron members have used the Catalites malware in their campaigns based on what we’ve seen so far. In the past few months, we have seen one or two fake apps per week attacking Android devices to make unsuspecting victims download the malware. Once downloaded, the criminals use very sophisticated social engineering tricks to get credit card information and possibly the ability to get into the victim’s bank account.
How does it get on your device?
While we are still investigating the details of this malware, here is what we know: this malware gets “dropped” onto your device after you download an app from a third-party app store (not official shops like Google Play) or from malicious adware (malvertisements) or phishing sites. Once dropped onto your Android device, the malicious app looks like the icon seen in the screen below and is titled “System Application.”
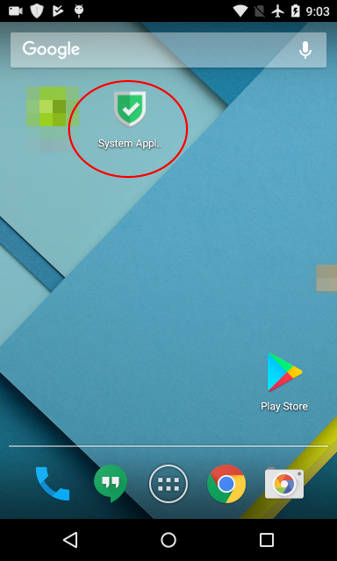
How does it trick you?
When you click the malicious “System Application” app icon, it will ask you for admin rights. If you grant those permissions, the malware begins its work. The icon for the (fake) app you downloaded disappears and then, three familiar-looking, trusted app icons get dropped onto your home screen: one for Gmail, one for Google Play, and one for Chrome.
![]()
The 3 new icons appear on your home screen for Gmail, Google Play and Chrome.
The malware author uses two sophisticated “social engineering” techniques to encourage you to open one of these three apps in order to display a fake overlay that invites you to enter sensitive information like your credit card. Cybercriminals are counting on the fact that you easily input credit card info for respected companies that you likely buy from regularly. Specifically, these techniques are:
- Creating mirror icons of three well-known apps: Gmail, Google Play and Chrome
- Creating a notification that cannot be removed that links you to a fake “sign-in” to your account
By placing these apps on the home screen, the user is more likely to open them, activating the malware so that the criminal can steal sensitive information.
_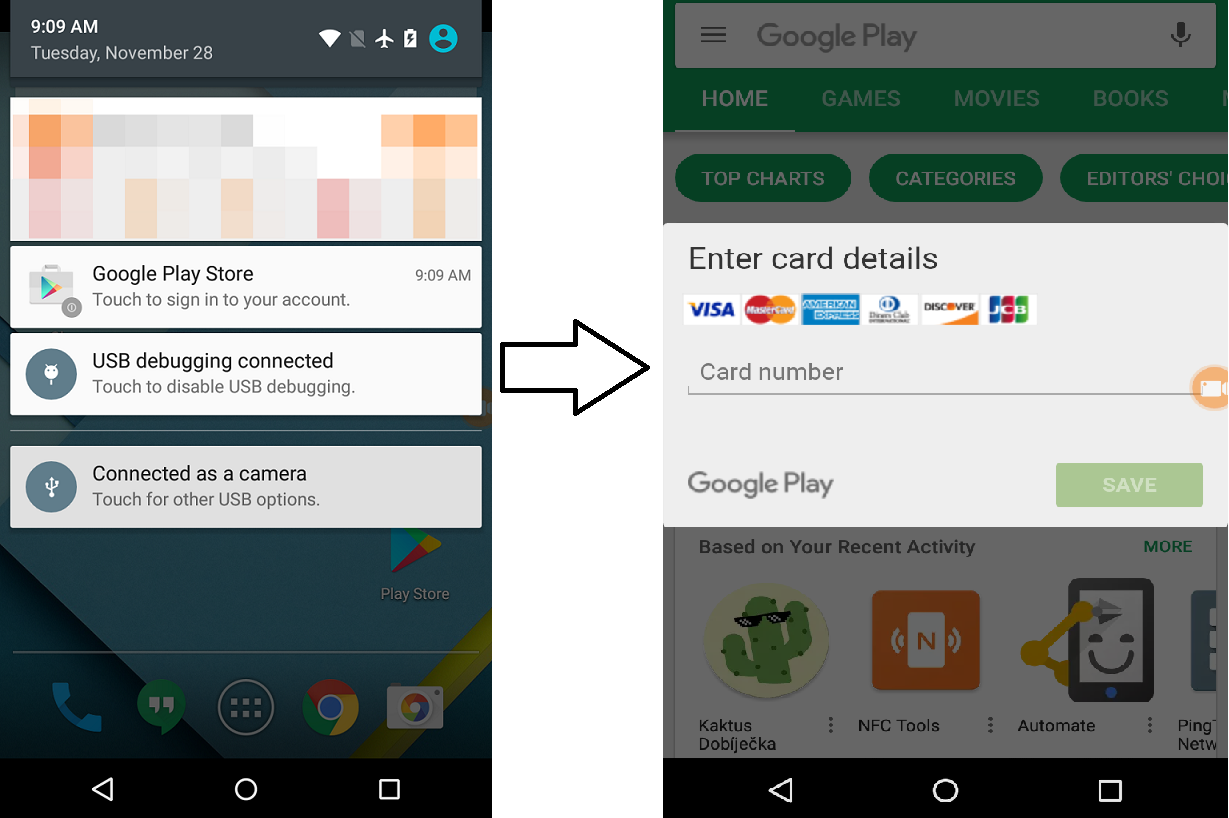
_
First you click “Google Play Store” notification;
then it asks for your credit card number.
Targeting over 2,200 financial institutions
Worse still, this piece of malware can also go after your bank account login details. This malware has the ability to pose as over 2,200 banks and financial institutions. It does so by adopting the logo and mobile application name of a bank used in the Google Play Store, allowing the author to use simple templates to harvest username and password or credit card information. The overlay is HTML-based and not as sophisticated as other Android banking malware such as LokiBot, Red Alert, or Exobot, but the power here is clearly in the shotgun approach: using simple phishing overlay screens, the criminals are able to target many more users, increasing their likelihood of financial gain.

Above shows examples of the fake overlay screens
that pull in the logos of actual banks.
Once you open your own banking app, the malware activates and places a fake overlay on your actual banking app, tricking you into entering your bank login details and also your credit card info. Once you provide this, they have access to your account and credit card.
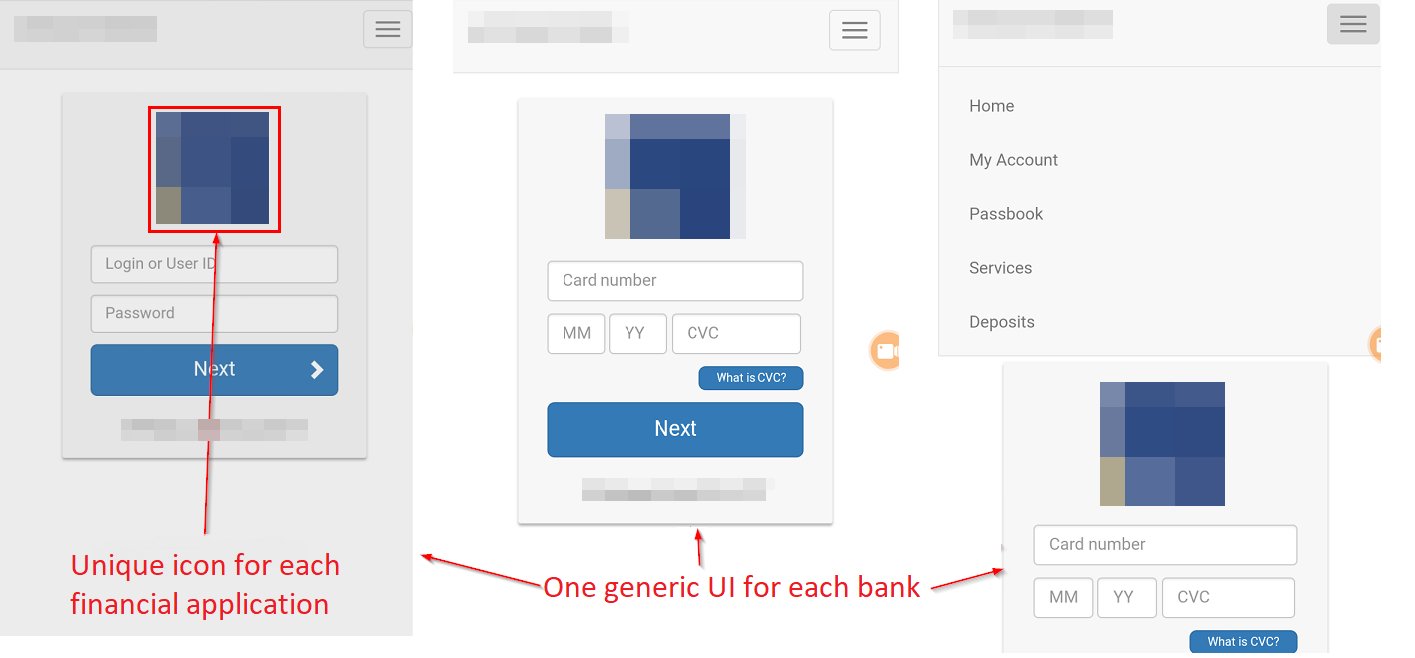
If your bank is one of the 2,200 targeted financial institutions, the app pulls in the logo of your bank to make the overlay look official.
Catelites Bot - Airbank example
Furthermore, it appears to have a host of other functions built in, though not yet activated. These include intercepting all incoming and outgoing SMS messages, setting ringer and stream volume to mute, and retrieving all running tasks from other apps. In addition, it can persistently ask for specific admin rights that could wipe data from your device or even lock you out completely.
Technical Information
=====================
- Intercepts all incoming and outgoing SMS messages
- Retrieves running tasks, phone number, IMSI, device model, android version, installed applications
- Sets ringer and stream volume to mute so the user doesn’t hear sms notifications
- Hides main application icon from launcher to stay stealthy
-
Asks for device admin privileges in order to become persistent and get functions like:
- Wipe Data
- Lock the device
-
Force a new unlock password for the device
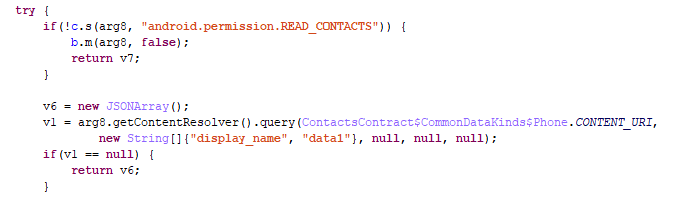
- Queries phone numbers from contacts
- Get SMS and MMS message conversations
Sets ringer and stream volume to mute in order to suppress sms notifications:
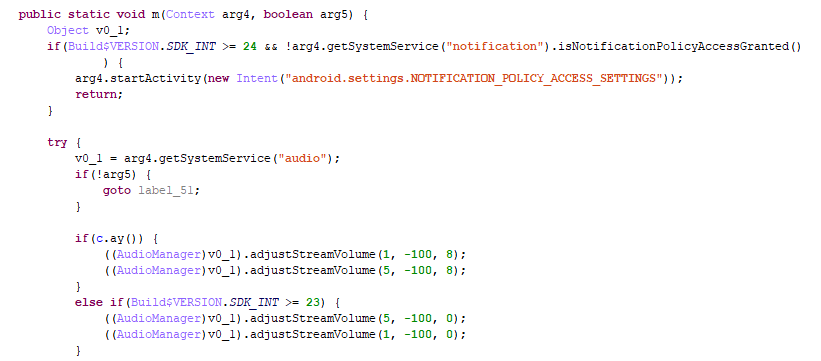
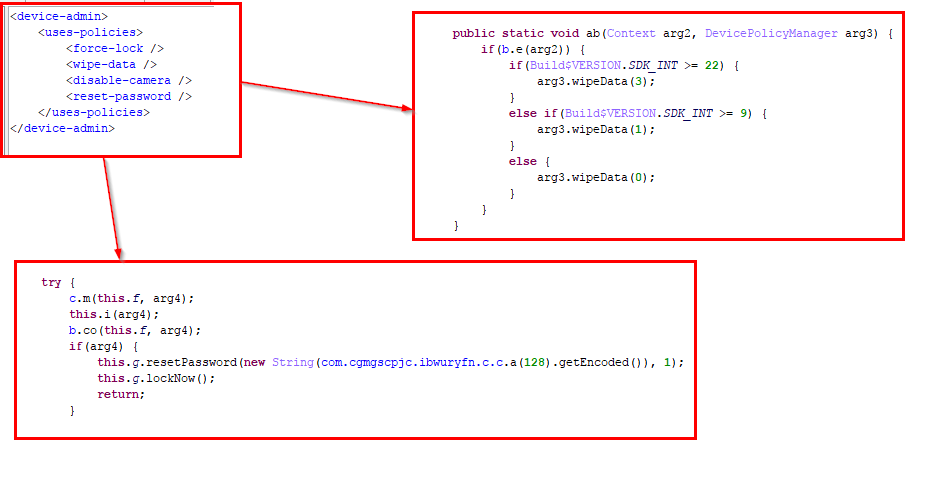
Admin privileges
Asks for device admin privileges in order to become persistent and get functions like Wipe Data, lock the device and force a new unlock password for the device:
Queries phone numbers from contacts:
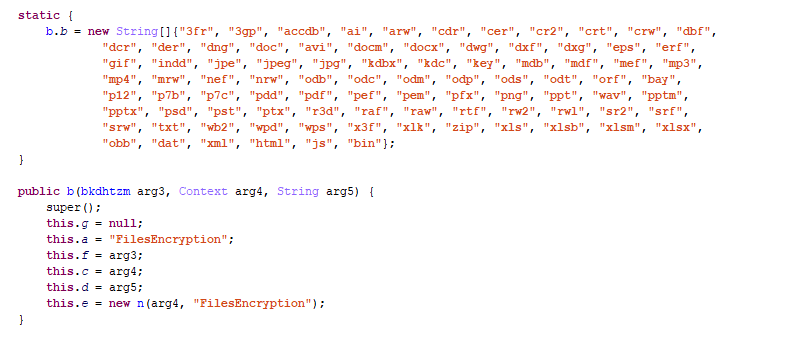
The Trojan has code to encrypt a big batch of file extensions with AES. The encrypted files will usually be renamed with the original name and a different extension “.cat”.
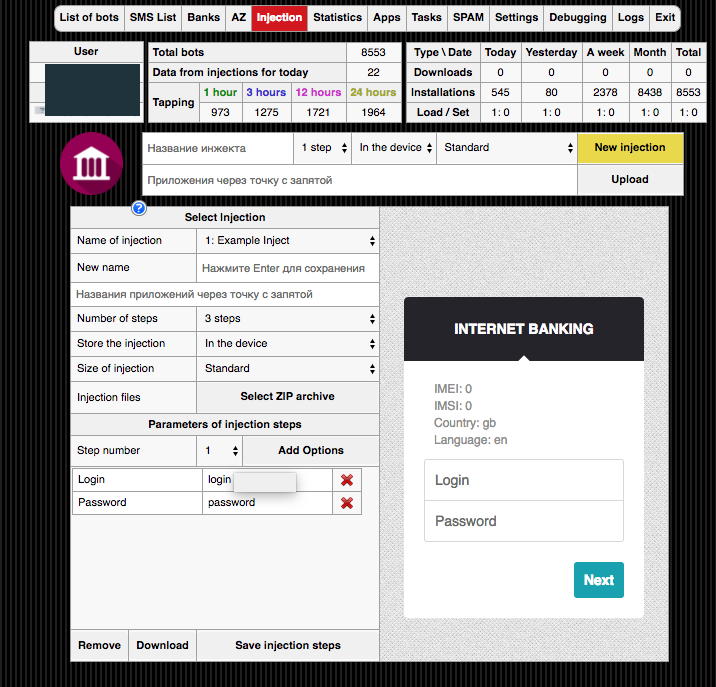
On December 8th 2017 a single botnet (C&C: 195.54.163.91) obtained 8553 bots in less than a month as shown in the panel of the C&C server.
The panel picture also shows similarities with the panel from the research that GroupIB did together with law enforcement to take down the “Cron” crew. We have no hard evidence linking Catelites actor llyamov to Cron but it is likely that Cron members have used the Catelites malware in their campaigns based on the exact Panel and bot similarities. The screenshot of the panel below also shows how easy it is to adjust the general overlay HTML (inject).
IOCs
SHA-256
Package Name
0e741a21228f4f7ffdbb891524f3a246b60bee287965a74fe15009127f6de280
net.feeteyemountain.houseracerlangtree
14c7e547cb8dc8f5d629725fdbdd2e8c33693dd407b2f36cd03c613e59af2cc7
net.friendsuperanswerland.foodfootmonth
efe6d86d7482fbcb5b1e7e12e22c2b086e4ec988939ebdffc9d363413e5a3326
net.windclockmailsentence.doorpageperson
bf6a4b8c24cd4cf233137dcee735bc33849d34e659ec2fa5e0fa9b425fee9b4e
net.bodywooddoodle.mountainfriendeast
e174dd174c5e21daa86064562aaf274d3f6fe84f4a3970beed48c02c3b605d58
net.songtablepicture.nightrocksciencemen
b81e0b6fe123b8d4cf7d99c20de1c694360d146bf80d9490b1b0325a00bf7f5a
net.manmothersouth.manbooksoundangry
0c50311ee3e30fe5be1b863db1b60b32bc9afa8d4264b852a836220751c7e3b2
net.herfarmsunhead.angryspacefile
d8452b39b1962239e9dbe12e8a9d8d0ee098b9c8de8a8d55b5a95b67b552102f
net.homeclasswindwater.daymaildayeye
53dc796e2e77689b115701a92ad2bdaeb0c7a4e87bc9e9a0bbeda057b77e22ee
net.productmotherfire.sentencerockdeveloper